TheHarvester
A powerful tool for OSINT
OSINT
Osama Shalhoub
1/22/20252 min read
Introduction
Open Source Intelligence (OSINT) is an essential practice in cybersecurity. Whether for penetration testing or investigations, having effective tools is crucial. Among key OSINT tools, TheHarvester stands out for its ability to collect public information during the reconnaissance phase. It is particularly useful in penetration testing to gather data on a target from publicly accessible sources.
To better understand what OSINT is, you can refer to my blog post dedicated to this topic. But in short, OSINT (Open Source Intelligence) refers to the collection and analysis of publicly available data from sources such as websites, social media, search engines, and databases. It is widely used in cybersecurity, ethical hacking, and digital investigations to gather intelligence without intrusive methods.
What is TheHarvester
TheHarvester is designed to retrieve publicly available data on a target domain using various information sources. It can collect email addresses, hostnames, subdomains, and IP addresses from multiple sources, including Bing, Yahoo, DuckDuckGo, Shodan, Brace.
This tool is particularly useful for identifying email addresses linked to a domain and mapping associated subdomains, providing valuable insights during reconnaissance and security assessments.
Using APIs in TheHarvester
By default, TheHarvester can query certain public sources without requiring additional configuration. However, to fully leverage its potential and access more detailed results, it is often necessary to configure API keys for certain databases and search engines.
Services like Shodan or VirusTotal provide advanced information but require authentication via an API. However, this topic will not be covered in this blog.
Exemple
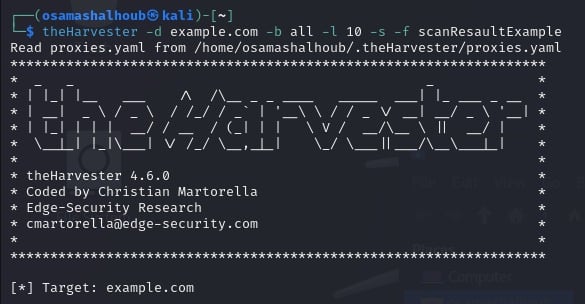
The following command performs an information search on the target domain example.com using all search engine, the search engine Shodan, limiting results to 10, and storing them in a file named scanResultExample
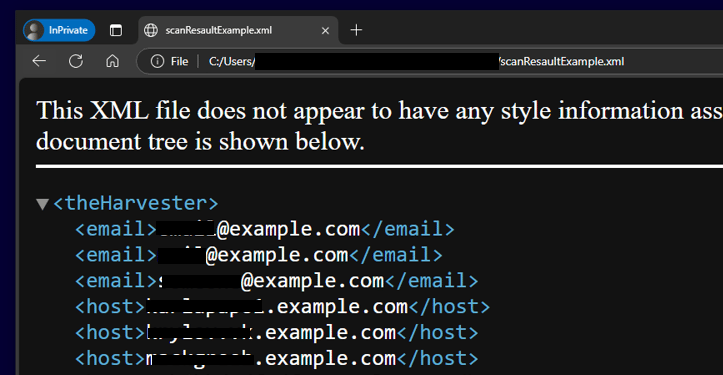
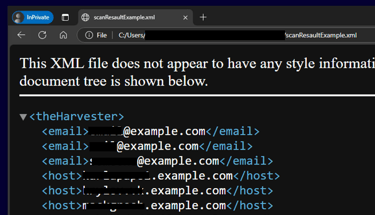
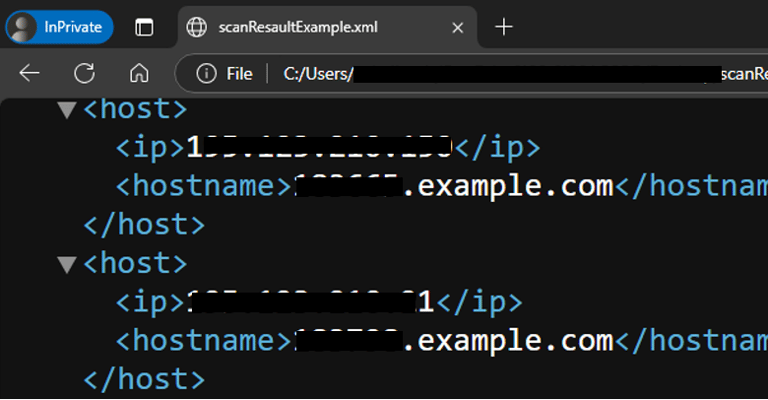
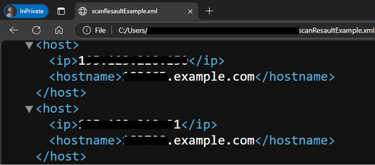
Use Cases
Pentesting and Reconnaissance: An excellent way to obtain basic information and an overview of an organization's exposed data before conducting a penetration test.
Monitoring and Cybersecurity: It helps track data leaks and verify compromised email addresses
How Can Companies Protect Themselves?
To prevent tools like TheHarvester from collecting too much sensitive information, companies can implement several protection strategies:
Implementing Security Policies: Reducing the publication of public email addresses and using generic addresses to limit employee exposure.
Employee Training: Educating staff about the risks associated with disclosing sensitive information online.
Configuring Search Engines: Requesting the removal of indexed information through tools like Google Search Console.
Regular Monitoring and Audits: Checking what information is publicly accessible online and using monitoring tools to detect leaks.
Conclusion
TheHarvester is a powerful tool for collecting public information. Easy to use and efficient, it allows rapid data retrieval on a target by leveraging publicly accessible sources. However, it must be used with caution and in compliance with applicable laws. Companies should implement strategies to limit their exposure and mitigate risks related to sensitive data disclosure.
Sources
Cyberie.com - What is theHarvester? - ABHIJITH
Youtube.com - 2.2.3 Activity Add API Keys to theHarvester - GNK Projects


