Scam Email from myself
Blackmailing myself to myself via email
CYBERSECURITY
Osama Shalhoub
9/1/20253 min read
More and more often, important emails or even simple messages to check end up directly in the “Junk or Spam Email” folder. That’s actually why I added this folder to my favorites. Don’t worry, this detail is important for what comes next.
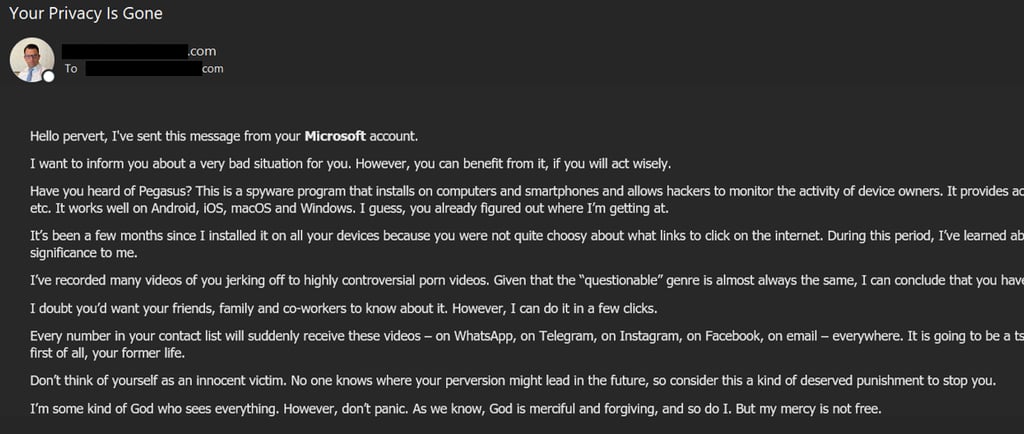
One evening, while checking my emails, I came across one in this particular folder. The subject line read “Your Privacy is Gone” I opened the email and discovered that it seemed to have been sent from my own address to myself. Indeed, both the sender and the recipient were the same as my email address.
The content explained that someone had supposedly hacked my mailbox, had access to compromising information, and was threatening me in exchange for money… a classic phishing attempt.
However, several elements quickly convinced me that it wasn’t credible:
The message didn’t appear in my “Sent Items” folder. Because, as with every email sent, a copy of the email must appear in this folder.
The message was in the junk emails folder.
The content looked like a simple copy-paste from existing scam templates.
Finally, the email mentioned I only had 48 hours to transfer money before the hacker would share compromising photos of me. But 48 hours passed, and my family never contacted me about receiving such photos.
More Technical Analysis of the Email
An email is a bit like a photo: it contains hidden metadata. In the case of an email, this information is found in the header.
To view it, you simply open the email, go to File by using Outlook App > Properties, then the dedicated tab. There you’ll find all the useful details. All you need to do is copy the information and paste it into a text file for analysis.
By analyzing the email, several technical elements show that it didn’t actually come from my mailbox.
IP address of the sending server
First, the IP address used to send the message is 142.111.56.145. Problem: this IP doesn’t belong to Microsoft servers. Microsoft publishes the official ranges of its Outlook/Hotmail servers, which usually fall within well-known blocks such as 40.x.x.x or 52.x.x.x (among others). The address 142.111.56.145 is completely outside Microsoft’s ranges, confirming the email didn’t come from their infrastructure.
SPF (Sender Policy Framework)
Second, we can check the SPF (Sender Policy Framework) result. SPF is an authentication mechanism that verifies whether the server sending an email is authorized to do so for a given domain.
By analyzing the headers, we can clearly see the result is FAIL and he is even kind enough to tell us the IP address that was used to send the email.
spf=fail (sender IP is 142.111.56.145)
In other words, server 142.111.56.145 attempted to send an email while pretending to be hotmail.com, but it’s not authorized at all. As mentioned earlier, this IP doesn’t belong to Outlook/Hotmail servers. If it had been a Microsoft IP, the test would have passed without issue.
Here’s an example of a legitimate email I sent, showing a valid SPF status:
spf=pass
DMARC (Domain-based Message Authentication, Reporting, and Conformance)
We also see that the DMARC test failed:
dmarc=fail action=none header.from=hotmail.com
DMARC is like an extra verification layer that cross-checks authentication information. Here, it confirms that the email is not legitimate.
On a credible email, it should look like this:
dmarc=pass
DKIM (DomainKeys Identified Mail)
Another important point in the analysis is DKIM (DomainKeys Identified Mail). This mechanism adds a digital signature to outgoing emails. The receiving server can then verify that:
The message wasn’t altered in transit.
The signing domain is indeed the one that sent the email.
In a legitimate Hotmail/Outlook email, you’d see something like:
dkim=pass (signature was verified) header.d=outlook.com
But in my fraudulent email, it clearly shows:
dkim=none (message not signed) header.d=none
This proves the message wasn’t signed by Microsoft. If it had truly come from my Hotmail account, there would necessarily have been a valid DKIM signature.
The sending server
Finally, by reading the following header line, we can see the real server that sent the message:
Received: from clearglow.net (142.111.56.145)
So, it’s not even a Microsoft server, but a third-party server (probably compromised or deliberately used to send spam).
How Did They Use My Address?
This technique is called email spoofing.
The From: field in an email can be falsified, just like on a paper letter where anyone can write your name as the sender. As a result, the email looks like it came from me, but in reality, it was sent from another server.
Mechanisms like SPF, DKIM, and DMARC are designed to detect this kind of fraud. In this case, all three failed, proving it was spoofing and not an actual hack of my mailbox.
In any case, I know that unfortunately my email address is floating around somewhere on the internet. This is unfortunate news, but guessing someone's email address these days is very simple. All you need to know is their first and last name.
Sources
Cybersmart.co.uk - “Note to self” phishing scams explained - Author unknown
https://cybersmart.co.uk/2025/05/note-to-self-phishing-scams-explained/


